Exploring the Concept of Zero Trust Security
In today’s fast-evolving digital landscape, where cyber threats are on the rise in terms of frequency and complexity, traditional security models have proven to be insufficient in safeguarding sensitive data and digital assets. In response to this growing challenge, a groundbreaking approach called Zero Trust Security has emerged, reshaping how organizations approach and implement their cybersecurity strategies. By challenging conventional notions of trust and adopting a data-centric, comprehensive security paradigm, Zero Trust Security offers a fresh perspective on ensuring information security in our interconnected world.
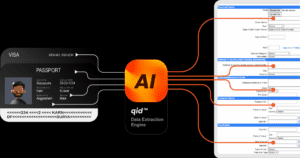
Download:- India’s 1st ID Gateway – qid
Understanding Zero Trust Security
At its core, Zero Trust Security is based on the principle of “never trust, always verify.” Unlike traditional security models that relied on a fortified perimeter, Zero Trust Security operates under the assumption that threats can originate both externally and internally. This approach is grounded in the understanding that data breaches can occur at any point within the network, necessitating a continuous process of verification and authentication.
The key principles of Zero Trust Security can be summarized as follows:-
- Verification and Authentication: In the Zero Trust model, every entity attempting to access resources undergoes continuous verification and authentication. This includes users, devices, applications, and processes. By subjecting all entities to scrutiny, organizations can ensure that only authorized entities gain access.
- Least Privilege: Zero Trust Security adheres to the principle of least privilege, which means users and systems are granted the minimum level of access required for their tasks. This approach minimizes the potential impact of a breach by restricting an attacker’s ability to move laterally within the network.
- Micro-Segmentation: Networks are divided into smaller segments, each with its own set of controls and security measures. Communication between these segments is carefully managed to prevent unauthorized access and limit the extent of breaches.
- Continuous Monitoring and Analysis: Real-time monitoring of network activity, user behaviour, and data flow is a cornerstone of Zero Trust Security. Any deviations from established patterns trigger alerts, enabling swift responses to potential security incidents.
Transforming Cybersecurity Landscape
- Adapting to Modern Work Environments: Traditional security models were built around centralized offices. However, with the rise of remote work, mobile devices, and cloud computing, these models have become inadequate. Zero Trust Security accommodates these changes by focusing on user and device identity, regardless of their location.
- Mitigating Insider Threats: Insider threats, whether deliberate or accidental, pose significant risks. Zero Trust acknowledges that trust should not be assumed solely based on internal status. Every entity, including employees, should undergo the same verification and access control processes.
- Securing Cloud and Hybrid Environments: The cloud introduces complexity to cybersecurity. Zero Trust’s emphasis on identity verification and continuous monitoring aligns well with the dynamic and distributed nature of cloud environments.
- Managing Third-Party Access: Organizations frequently collaborate with external partners and vendors, introducing potential vulnerabilities. Zero Trust principles extend to third parties, ensuring their access is verified, controlled, and monitored like internal users.
- Enhancing Incident Response: Zero Trust’s continuous monitoring and real-time alerts empower organizations to respond swiftly to security incidents. Rapid identification and containment of breaches minimize potential damage.
Challenges and Implementation Strategies
While Zero Trust Security offers significant benefits, its implementation poses challenges:
- Complexity: Adopting a Zero Trust model requires a paradigm shift in mindset and operational processes. It necessitates a thorough evaluation of existing security practices and infrastructure.
- User Experience: Balancing stringent security controls with user convenience is crucial. Excessive measures could hinder productivity and user satisfaction.
- Legacy Systems: Integrating Zero Trust principles into legacy systems may demand substantial modifications or even system replacements, which can be resource-intensive.
- Data Privacy and Compliance: Organizations must navigate regulatory frameworks and data privacy considerations while implementing Zero Trust measures. Compliance with industry standards and regulations is paramount.
Looking Ahead
The adoption of Zero Trust Security marks a fundamental shift in organizations’ approach to cybersecurity. In a rapidly advancing technological landscape, where cyber threats evolve, this approach offers a proactive strategy that aligns with modern computing environments. Collaborative efforts among safety professionals, IT teams, and organizational leadership are crucial for successful implementation and ongoing adherence to Zero Trust principles.
The journey toward Zero Trust Security requires commitment, investment, and continuous learning. While challenges exist, the potential benefits—enhanced resilience against cyber threats, improved incident response capabilities, and better protection of critical data—make it a compelling strategy for organizations aiming to secure their digital assets in a dynamic and interconnected world. By embracing the concept of “never trust, always verify,” organizations can establish a more secure foundation for their digital future.
Also, read:- How businesses can use technology to support their business processes?